General information
With Java 17, weak Kerberos authentication is no longer officially supported.
This means that the RC4-HMAC and 3DES-HMAC used so far must either be replaced by AES keys or, which we do not recommend, the old outdated crypto model in krb5.config must be allowed again.
AES key (secure)
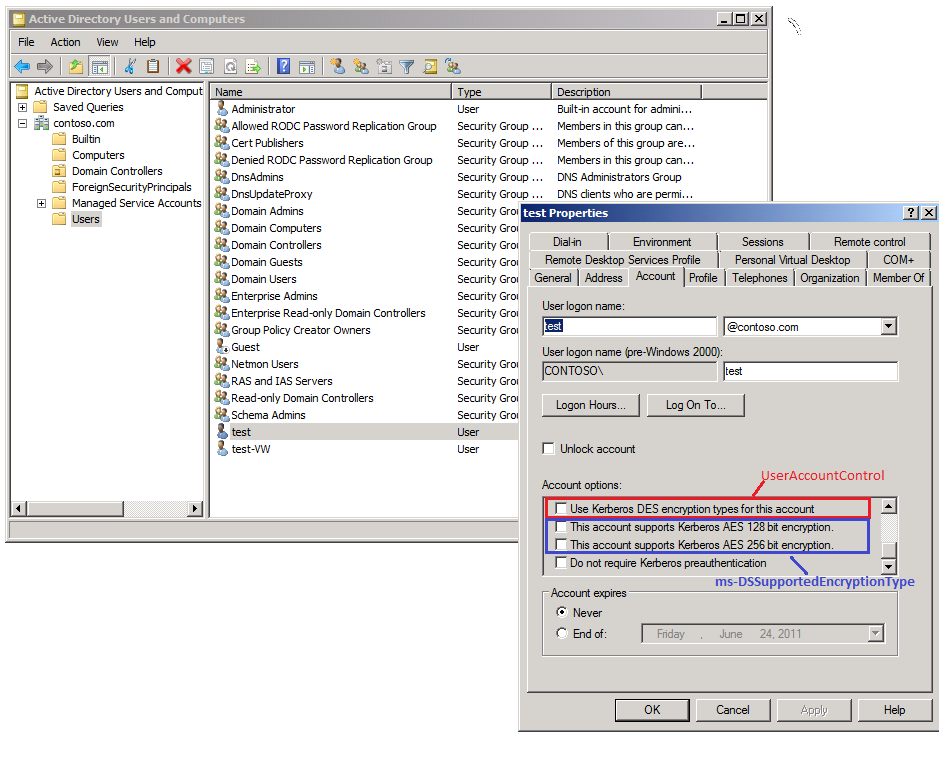
When switching to AES keys, changes in the ActiveDirectory are necessary.
The secure but more complex method:
- Enable AES encryption on the PreAuth and SSO users.
- Modify the krb5.config file: Delete the insecure ciphers RC4-HMAC and 3DES-HMAC.
Customise krb5.config (unsafe)
Open the krb5.config file and add the parameter allow_weak_crypto=true to the second line of the file.